 My six-year-old son wants to play Wild West. “I’ll be the outlaw,” he tells me. I make a poster that says, “Wanted: Dead or Alive.” I hang it by a magnet on the refrigerator. “Seriously, Mom? The fridge?” my child says. “A real sheriff would post it on Facebook.” As it turns out, my kindergartener is absolutely right.
My six-year-old son wants to play Wild West. “I’ll be the outlaw,” he tells me. I make a poster that says, “Wanted: Dead or Alive.” I hang it by a magnet on the refrigerator. “Seriously, Mom? The fridge?” my child says. “A real sheriff would post it on Facebook.” As it turns out, my kindergartener is absolutely right.
Law enforcement tools have evolved significantly over the years from wanted posters and milk cartons to police radios and now social media platforms like YouTube, Facebook, and Twitter. Police departments also use social media to find missing children, as well as alert communities about suspicious activities and crimes recently committed in their area. [Read more…]
 At first glance, there aren’t many differences between the iPad 2 and the 3rd Generation iPad – same size, same weight, same battery life – but what has changed has changed in a big way!
At first glance, there aren’t many differences between the iPad 2 and the 3rd Generation iPad – same size, same weight, same battery life – but what has changed has changed in a big way! Anything and everything you put over the Internet is subject to being spied upon. There’s no way to avoid this being the case. The way you control whether or not you are spied upon is by controlling what you put over the network.
Anything and everything you put over the Internet is subject to being spied upon. There’s no way to avoid this being the case. The way you control whether or not you are spied upon is by controlling what you put over the network. It’s not paranoia if they’re really out to get you. One nasty malware program or virus could wipe out your entire operating system. Along with your operating system, your photos, music, files and programs will go up in smoke as well.
It’s not paranoia if they’re really out to get you. One nasty malware program or virus could wipe out your entire operating system. Along with your operating system, your photos, music, files and programs will go up in smoke as well.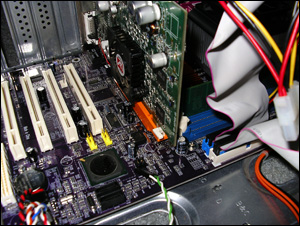 We live in an age where most people already use a computer on a daily basis – no arguments there, right? The problem is that only a fraction of these users know how to fix hardware issues without calling for a technician. That’s too bad, since there are many hardware issues that aren’t that complicated to handle by anyone. No worries though…
We live in an age where most people already use a computer on a daily basis – no arguments there, right? The problem is that only a fraction of these users know how to fix hardware issues without calling for a technician. That’s too bad, since there are many hardware issues that aren’t that complicated to handle by anyone. No worries though…